Hyperledger Indy [Part I] - Layer of Trust
In this series of articles, we will be discussing what Hyperledger Indy is, what are its main components and architecture, and how to deploy your own agent. So fasten your seat belts because we are about to begin our journey.
Introduction:
As we know that in the current era, we have two ways to prove our identity over the internet. One way is User ID/Email and password, another way is Single Sign On (SSO). Big organizations such as Facebook or Google maintain our identity and we use the provided APIs in our platform to receive the proof of the user's identity.
This model leads to data breaches and vulnerabilities and correlations. We no longer own our data and data breaches can expose our sensitive information. Other than that, one more problem that we face is verifying the issued credentials.
Therefore, in this article, we will discuss the Paper Credential Model and how the Verifiable Credential Model solves many problems regarding centralized identifiers and also what enables the layer of trust over the internet.
Paper Credential Model:
Before explaining the Paper Credential Model, first, let’s understand what actually a credential is.
A credential is basically an attested qualification issued to a person or entity by an organization that is competent. Examples of credentials are your national identity card, driver’s license, degree, or any kind of certificate.

Consider a scenario in which you have to prove that you are eligible to drive. The entity (holder) holds the credential which is the driver's license. An authorized organization (issuer) issues this credential. The holder presents the proof to the organization (verifier), which then verifies it. That’s the Paper Credential Model.
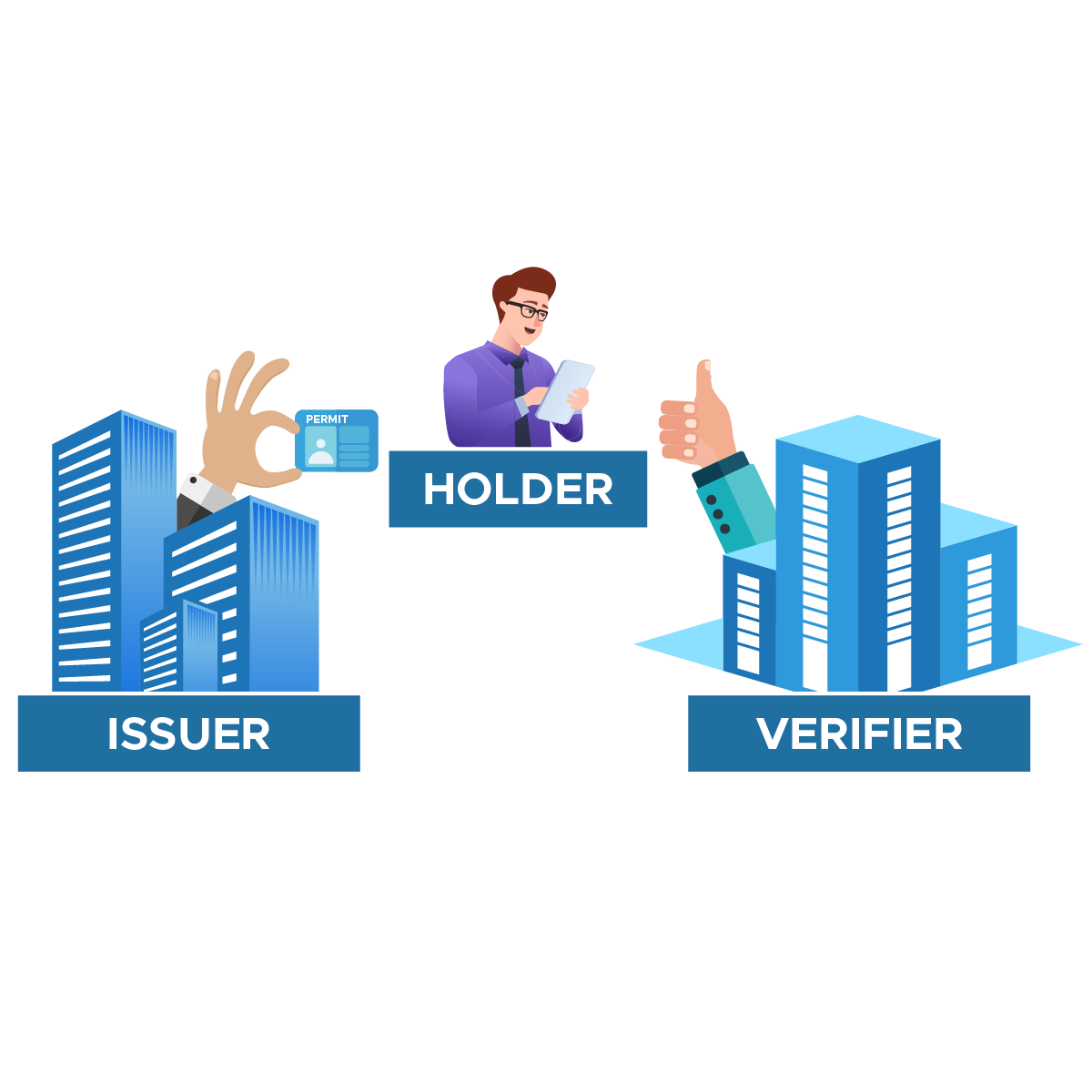
Ideally Paper Credential Model proves:
- Who holds the credential?
- Who issued the credential?
- Has someone altered or tampered the credential?
Disadvantages of the model:
One can easily forge or alter the documents, certificates, or any other kind of credential. In the modern world with modern technology, it's really easy for the person to even create fake credentials. And the verification process totally depends on the skills of the verifying organization.
Verifiable Credential Model:
The Verifiable Credential Model works in the same way as the Paper Credential Model which means:
- An issuer issues the credential to you.
- You hold those credentials in your (digital) wallet.
- The verifier requests you to present proof of that credential.
- The verifier checks the revocation status of the credential.
Before moving on, let’s understand one more term “Claim”. Credentials are a set of claims. Your driver's license is a credential but your name and other information are individual claims.
Verifiable credentials are not as simple as paper credentials that anyone can use. They are cryptographically encrypted documents. Calculations and algorithms run over these documents to verify these four attributes.
- Who issued the credential?
- The presenter owns the Claims.
- Claims have not tampered.
- Claims have not been revoked.
Verifiable credentials are stored in verifiable data registry (Blockchain). When a verifier asks for proof from the issuer he uses the information from the registry and performs cryptographic calculations to verify the four attributes. This cryptographic calculation and storing of the document make it hard to forge.
Trust layer over the Internet:
As we have discussed Paper Credential Model and how the Verifiable Credential Model is more secure, VCM is being enabled by some key concepts which enable this trust layer over the internet. So let’s discuss them.
Self Sovereign Identity:
The literal meaning of SSI is an identity that you control and own. There is no central organization that owns or controls your identity. In order to understand SSI more, let’s look at these principles of SSI:
- Every user must have an independent existence.
- Users must control their identities.
- Users must have access to their own data.
- Identities do not get expired or deleted.
- Users can transport the information linked to their identity to another service.
- Identities should not have any constraint over the usage.
Decentralized Identifiers (DIDs):
Decentralized Identifiers are the enabler and important components of verifiable credentials. The owners themselves create DIDs independent of any central authority. A DID looks like the following as per DID specification. It is similar to an HTTP address but the usage is different.
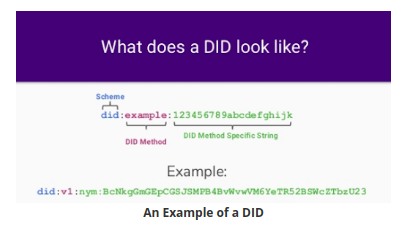
DID doc is the document that is linked to this specific pattern string. It contains the public key whose private key is owned by the owner, also a service endpoint through which we can communicate with the holder. A DID is like a URL, you can resolve your DID doc by using the DID resolver.
Following are some benefits of a DID:
- Provable
You can prove your identity through the DID you own. Because the DID doc contains the public key of which the private key you hold. Cryptographically no one can claim your DID until and unless you provide them your private key. - Non-Correlatable
One problem with the SSO model is that we are re-using one identity over every service. You can use your one DID for every service you use but the better way to avoid correlation is to remake a new DID for every service you use. - Secure Communication
DID doc contains a communication URL as well as a public key. So whenever we are communicating by using DIDs we encrypt the message with the public key of the receiver. This enables a layer of security also.
Zero-Knowledge Proof and Selective Disclosure:
Zero-Knowledge Proof means to prove the claim without revealing the DID or any correlating information. In a ZKP claim, the DID of the holder is not revealed. Only the DID of the issuer is revealed.
As we have mentioned above that credentials are a set of claims. It means that your driver’s license is a credential and your first name, last name, etc are individual claims. Now in today’s world when you are asked to present a claim to prove that you are above 18. Your other information is also disclosed including name and other relevant information in your credential.
But selective disclosure enables the user to disclose only relevant information in the presentation of claims. Selective disclosure and ZKP are both used together to ensure security and also the confidentiality of the data. The reason for this is that in SSI, data is owned by the user and the user decides how much information they want to share.
Agents and Wallets:
In the article, we have talked about terms like verifiable credentials, DIDs, public and private keys, etc. But where do they reside? How to manage them? What is the channel through which the DIDs communicate and present claims? Agents store them.
Agents and wallets are interchangeable terms. They have secure storage to manage DIDs, public and private keys, and verifiable credentials.
There are different types of agents. The most common one is “Mobile Agent”. For simple understanding, agents are software that is used to manage DIDs, wallet keys, and verifiable credentials. But agents are used for other purposes too. We won’t be diving deep into the technical details in this article.
Conclusion:
In this article, we have talked about the building components which provide the layer of trust over the internet. We have discussed two credential models. Also, we learned about SSI, DID, verifiable credential, and many other things that help to implement the Verifiable Credential Model and other things. We haven’t taken a deep dive technically into things yet but in the next article, we will take the leap of faith. Just to give you a sneak peek, we will discuss the architecture of agents, type of agents, and how Hyperledger Indy enables all of this with other Hyperledger tools.
Also read our series of articles on Setting up Hyperledger Fabric Network.
Xord is here to help you with your Blockchain projects. Connect with us at https://blockapexlabs.com/contact/